Gartner predicts that organizations’ IT teams will increase their level of software spend by nearly 12% in 2023.
This underscores employees’ growing appetite for software (SaaS applications) and the risks of failing to satisfy this desire. More specifically, if IT can’t provide employees access to the applications they need within a short time frame, employees may take it upon themselves to buy these applications.
While this might seem like a suitable solution, as employees can access the tools they need quickly and easily, it introduces several business risks.
We’ll discuss these risks in detail and offer a solution for addressing them. But first, let’s explain the phenomenon associated with this behavior: shadow IT.

What Is Shadow IT?
Shadow IT is when an employee uses a software application or device that the IT team doesn’t own or centrally manage. Since IT typically isn’t made aware of these applications and devices, they can’t respond accordingly.
Given its broad definition, shadow IT can take various forms. Common examples include:
- Working on a personal laptop or smartphone or using storage devices like external hard drives and USB drives (assuming your organization doesn’t have a bring-your-own-device, or BYOD, policy) to transfer network resources.
- Using a third-party SaaS application that IT hasn’t approved. These apps are permitted to access and exchange data such as profile info and location. This data access and exposure may allow cyber attackers to implant malicious code into the SaaS platform.
- Emailing employees, clients, or prospects from a personal email address. Sharing sensitive corporate information outside a company’s secure channels may lead to data governance, regulatory, and compliance issues.
- Employees installing extensions such as ad blockers and productivity extensions on browsers logged in using work accounts without IT approval. These extensions can access corporate data and sometimes alter it.
- Using cloud storage and file-sharing apps that the company doesn’t use, like OneDrive, Google Drive, and Dropbox, posing data leakage and unauthorized access threats.
Related: What are citizen integrators?
What Are the Risks of Shadow IT?
Here are just a few of the issues associated with shadow IT.
Security Risks
Employees almost certainly don’t take the same precautions in protecting their personal devices as they do with work-issued equipment. As a result, working from the former can lead to a wide range of problematic scenarios:
- An employee may not have set up a login to access their personal computer. This leaves your data and applications vulnerable if the laptop gets stolen.
- Assuming the device doesn’t have the proper anti-malware software installed and/or uses an outdated operating system, it’s largely unprotected from cybersecurity attacks.
- An employee may forget to download and use a VPN on their personal device. This leaves them exposed to unsecured networks when working in a coffee shop, airport, or other public space.
Compliance Risks
To build trust and credibility with prospects and clients, your organization must comply with widely recognized regulations, like GDPR, and regularly pass security audits, like SOC-2 Type II. Shadow IT doesn’t necessarily cause compliance issues or lead you to fail a security audit. However, it may leave your organization significantly more vulnerable.
Unnecessary Spending
In some cases, an application purchased via shadow IT overlaps with an existing point solution(s). The purchaser was simply unaware, either out of negligence or because they lacked a holistic view of their organization’s tech stack. In either event, this purchase is a redundant expense that could have been avoided had IT been involved.
Suboptimal Applications
Your team of IT professionals has likely created a comprehensive procurement process that ensures the tools purchased adhere to high-security standards and are best-in-class.
For instance, when evaluating a given tool, the requestor may need to provide information on:
- The tool itself
- The information it would store
- The certifications it has earned
- The individuals who would use it
- The use cases it would support
The requestor might also need to identify alternatives and compare all the options in terms of price, ease of use, etc.
Through shadow IT, employees can skip this evaluation, leading them to neglect better tools and ignore security gaps that can come back to hurt your organization.

Related: Why you should use a service desk chatbot (and how you can use it)
Data Loss
Since IT doesn’t establish a backup strategy for shadow IT applications, they’re susceptible to permanent data loss. In other words, events like data breaches could affect your organization even more, as a disaster recovery plan for these apps doesn’t usually exist.
Compromised Integrations
Your applications become vulnerable when integrated with a shadow IT application. For example, the shadow IT application can access and store sensitive data from connected applications—providing a potential attacker with an access point to that data.
Data Integrity
Without clean and accurate data, your organization will fail to make timely and appropriate decisions. For instance:
- Your reps may reach out to prospects who aren’t ready to buy while ignoring those who are
- Your customers may receive emails meant for prospects
- Your HR team may offer benefits to the wrong set of employees
Shadow IT can create these situations, as IT can’t oversee the access levels of these applications or uncover (and address) suspicious behaviors when any occur.
What Are the Benefits of Shadow IT?
Despite all of its issues, shadow IT isn’t all bad. Here are a few of the reasons why shadow IT can help your team:
- It can improve employee productivity. Since employees don’t wait for IT to approve their request for a given application, they can adopt it and leverage its functionality in their day-to-day work quickly. Moreover, they can select whatever applications they want, leading them to pick those that allow them to perform their work most effectively.
- It can strengthen your relationship with employees. Giving employees more influence over the applications and devices they use communicates, albeit implicitly, that you trust and value their judgment. This should go a long way in improving employee engagement, which, as ample research suggests, can boost employee performance.
- It can free up IT. By allowing IT to avoid reviewing application and device requests manually, they can focus on other business-critical work. This can be anything from implementing integrations and automation to troubleshooting and resolving incidents (although, ironically, shadow IT can cause many incidents).
- It can reveal opportunities for process improvement. Assuming your IT team discovers the applications and devices that fall out of their control, they’ll likely spot patterns in terms of the departments, regions, and even the specific end users who perform shadow IT. They can then work with these stakeholders to better understand why they performed shadow IT and how they can improve their provisioning processes on behalf of these teams.
- It can elevate your organization’s performance. Similar to our first benefit, when employees use the applications they prefer and are comfortable with, they’re more likely to make decisions and take actions that benefit your organization. This can take several forms: a sales leader can iterate on their team’s sales process based on the tool they acquire; the product team can begin to collect in-product feedback and use those insights to revise their roadmap; an SEO expert can conduct more in-depth analysis and identify more impactful keyword opportunities, etc.
How to Mitigate Shadow IT
You might ask yourself, “How can I reap the benefits of shadow IT while avoiding its drawbacks?”
We’ve addressed this first-hand through the use of a platform bot we call “Firefighter.”
Through Firefighter, employees can identify the applications we currently have and request access to any. They can also use the chatbot to file a ticket to procure a specific application or device. Once these requests take place, Firefighter notifies the appropriate approvers. The approvers review the requests, and they can approve or reject any requests with the click of a button.
Perhaps the best part about Firefighter: It allows our employees to make these requests and approvals all within our business communications platform—which happens to be Slack. Let’s take a closer look at how it can work when one of our employees wants to access a specific application.
1. The employee navigates to Firefighter in Slack and sees a homepage with various options. The employee goes on to select Request for Apps.
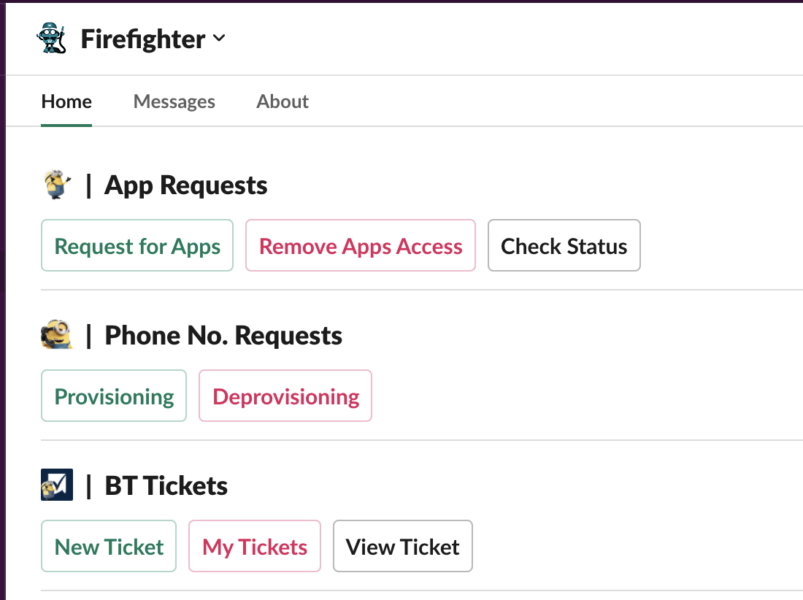
2. A modal (or pop-up) presents the employee with a few options. These include selecting the beneficiary (where they’d list themselves), the provision date, the app, and the reason behind their request.
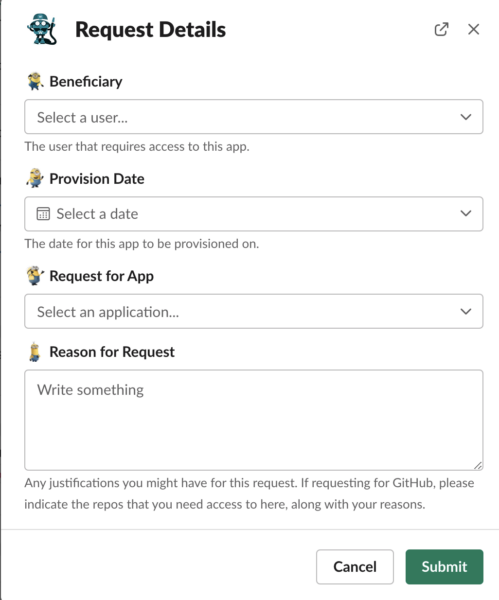
3. Once submitted, the employee’s manager receives a message from Firefighter. The message presents all of the details around the request, and it would allow them to approve or reject it with the click of a button.
4. Once approved, IT gets notified via a specific channel, and the provisioning is carried out automatically via OneLogin.
5. The requestor receives a notification from Firefighter, informing them of the request approval and successful provisioning.
OAuth and Shadow IT
OAuth is a double-edged sword that can mitigate or enable shadow IT, depending on how you implement it. Granting extensive OAuth permissions to third-party apps without IT oversight can pose a security challenge. When you authorize access to core apps, you allow third-party apps to collect and store company data. So, company data is at risk if an attacker gets inside the app.
At the same time, you can use the OAuth protocol to address some shadow IT risks, such as security and compliance. For example, you can use OAuth to identify the apps authorized to access corporate data.
Resource owners use OAuth as the authorization server to control access to resources. They grant third-party applications temporary refresh tokens and access tokens to access user data, not usernames or passwords. With OAuth access tokens, third-party apps get limited access time, reducing security risk. Furthermore, if an attacker steals an access token, they only have limited time to use it.
Improperly managed access tokens can allow unauthorized access and enable attackers to compromise accounts and data. OAuth allows the IT team to revoke refresh tokens and access tokens if they notice suspicious activity that may breach regulatory compliance guidelines. By providing secure token-based authentication, OAuth ensures the protection of user data, helping comply with industry regulations.

Implement your own version of Firefighter with Workato
Despite its drawbacks, shadow IT provides many benefits, including improving employee productivity and enhancing the employer-employee relationship. It puts security and IT teams to the test of enhancing security while protecting the value that shadow IT brings. Doing so requires using authentication protocols or technologies such as Firefighter. Workato enables you to implement your own version of Firefighter and enjoy the benefits of Shadow IT while avoiding shortcomings. Workato, the leader in enterprise automation, offers Workbot, a customizable platform bot that lets you bring automation to Slack, Microsoft Teams, or Workplace from Meta. Request a demo today to see how we can address your needs.

Implement your own version of Firefighter with Workato
Workato, the leader in enterprise automation, offers Workbot, a customizable platform bot that lets you bring automations to Slack, Microsoft Teams, or Workplace from Meta.