In today’s digital landscape, where cyber threats loom large, organizations face the daunting task of safeguarding their data and systems. With cyberattacks becoming more sophisticated, businesses are under constant threat. According to a recent Gartner Survey, a staggering 88% of boards now view cybersecurity as a significant business risk. Enter the unsung heroes: the IT Team, SOC Team, BT Team, SecOps Team, and others who work tirelessly day and night to shield organizations from these threats.
However, the challenges are immense. The State of SOAR Report highlights that approximately 11,000 security incidents are handled by SecOps teams every day on average. A whopping 70% of their time is spent on manual investigation, triage, and response. These demands not only strain resources but also take a toll on the mental health of cybersecurity incident responders, with 65% seeking mental health assistance, according to the IBM Security Incident Responder Study.
What is SOAR?
Security Orchestration, Automation, and Response (SOAR) tools are a beacon of hope in this scenario. They combine inputs and alerts from various security tools into a single, manageable solution, extending network visibility and simplifying threat identification and remediation. The goal of SOAR platforms is to enhance the efficiency of physical and digital security operations.
Gartner Definition: SOAR technologies help SecOps teams collect data. For example, SIEM alerts and other inputs so teams and machines can run analysis and triage incidents. SOAR tools allow an organization to define and standardize incident response procedures in a digital workflow format.
Benefits of SOAR:
SOAR platforms offer a multitude of advantages for enterprise security operations teams:
Enhanced Threat Context: By integrating diverse tools and systems, SOAR platforms gain real-time threat data and analysis, providing invaluable context for security teams.
Swift Incident Detection and Response: SOAR significantly reduces the time to detect and respond to security threats. Automated playbooks enable rapid identification and mitigation of threats.
Streamlined Operations: Standardized procedures and automated playbooks empower security teams to handle a higher volume of threats, ensuring consistent remediation efforts.
Cost Savings: SOAR tools supplement security teams, reducing costs associated with manual threat analysis and response efforts.
Workato’s SOAR Approach
Workato’s SOAR Accelerator provides a streamlined solution for organizations looking to bolster their cybersecurity posture. Using pre-built recipes, Workato’s platform enables automation in security operations. These recipes, based on low-code and no-code capabilities, leverage a vast array of ready-to-use connectors, linking seamlessly with numerous applications.

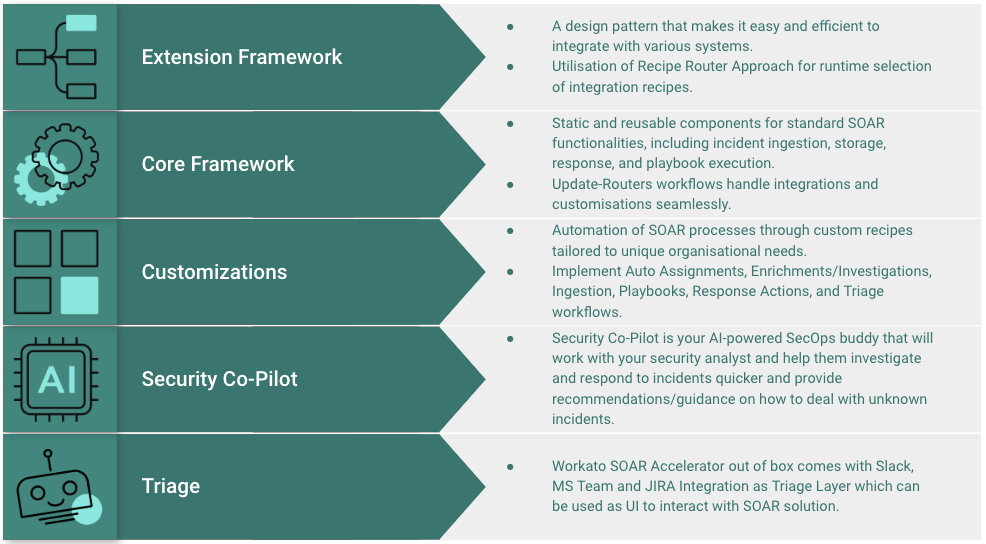
Critical Components of Workato’s SOAR Accelerator:
Why Use Workato’s SOAR Accelerator?
Efficiency Boost:
Workato’s SOAR Accelerator streamlines and automates security operations, reducing the manual effort required for incident detection, response, and resolution.
Rapid Incident Response:
The prebuilt recipes and automation workflows enable swift and automated responses to security incidents, minimizing the time it takes to detect and mitigate threats.
Flexibility and Customization:
Workato’s SOAR Accelerator provides a flexible framework that allows companies to customize automation workflows based on their unique security needs and the applications they use.
Integration Capabilities:
With 1,200+ ready-to-use connectors, Workato’s SOAR Accelerator seamlessly integrates with a wide range of applications, extending its capabilities and ensuring comprehensive coverage.
Application Agnosticism:
The accelerator is designed to be application-agnostic, allowing companies to change or add applications with minimal adjustments, providing scalability and adaptability to evolving security landscapes.
Scalability and Extension Framework:
Workato’s SOAR Accelerator is built with scalability in mind. The Extension Framework efficiently integrates various systems, and the platform can handle the growing demands of security operations.
Centralized Management:
The platform consolidates multiple security systems into a unified interface, simplifying management tasks and providing a centralized view for security operations teams.
Cost Savings:
Automating security processes with Workato’s SOAR Accelerator often leads to cost savings compared to manual efforts, making it a cost-effective solution for enhancing cybersecurity operations.
Real-time Threat Context:
By integrating with various tools and systems, Workato’s SOAR Accelerator gains real-time threat context, providing security teams with comprehensive insights for more effective decision-making.
ML Capabilities: The platform’s Machine Learning (ML) capabilities enhance incident handling, providing intelligent recommendations and automating actions based on AI-driven insights.
Comprehensive Reporting and Analysis:
Workato’s SOAR Accelerator streamlines reporting, analysis, and data management, enabling effective security policies, fostering collaboration, and supporting informed decision-making.
Applications of Workato’s SOAR Accelerator
Security teams face a myriad of challenges, from phishing attacks to insider threats and malware intrusions. Workato’s SOAR solution gives organizations the power to automate a wide range of security operations to supercharge their response:
Phishing Email Detection and Response:
Automate the identification and analysis of phishing emails. Implement actions such as quarantining suspicious emails, alerting security teams, and initiating investigations, all without manual intervention.
Insider Threat Monitoring:
Continuously monitor user activities within the network. Automated alerts and responses swiftly address unusual behavior, ensuring immediate action against potential insider threats.
Malware Analysis and Containment:
Automate the analysis of detected malware, gathering valuable insights about its behavior. Isolate infected devices promptly and enhance future threat prevention strategies based on automated malware analysis.
Vulnerability Scanning and Patch Management:
Automate vulnerability scans, identify vulnerable systems, and prioritize patch deployments. Ensure systems are up-to-date and secure by automating the patching process.
Automated Incident Response Workflows:
Implement tailored incident response workflows. Enable automated identification, containment, eradication, recovery, and post-incident analysis, significantly reducing response time and minimizing manual efforts.
Security Policy Enforcement:
Automate the enforcement of security policies, ensuring compliance with industry regulations and internal standards. Implement automated access control, password policies, and other security measures across the organization.
Data Loss Prevention (DLP):
Automatically detect and prevent sensitive data from leaving the network. Implement rules to block or encrypt data based on predefined policies, safeguarding critical information.
SIEM Integration and Correlation:
Integrate with SIEM systems to correlate security events across multiple sources—Automate responses based on correlated data, allowing the detection of complex attack patterns and immediate action.
Incident Reporting and Documentation:
Automate the documentation of security incidents, including event details, actions taken, and resolution. Generate incident reports automatically for compliance purposes, ensuring thorough documentation of security events.
User Access Control and Authentication:
Automate user access provisioning and de-provisioning based on role changes. Implement multi-factor authentication and automate login monitoring for enhanced security and identity verification.
Cyber security is a never-ending challenge for modern business, but as threats evolve, so do the tools we have to fight them. Workato’s SOAR Accelerator offers top of the line security automation capabilities that will allow you to put your organization’s best foot forward with confidence.