Recipe highlight: enhancing asset security and compliance with automation
Enhancing Asset Security and Compliance
Safeguarding new IT assets by performing vulnerability scans
Maintaining an up-to-date inventory of assets while ensuring their compliance and security is paramount. Our innovative automation not only optimizes asset inventory management but also fortifies data security and compliance, eliminating manual tasks and promoting a more efficient, secure infrastructure.
How the Automation Works:
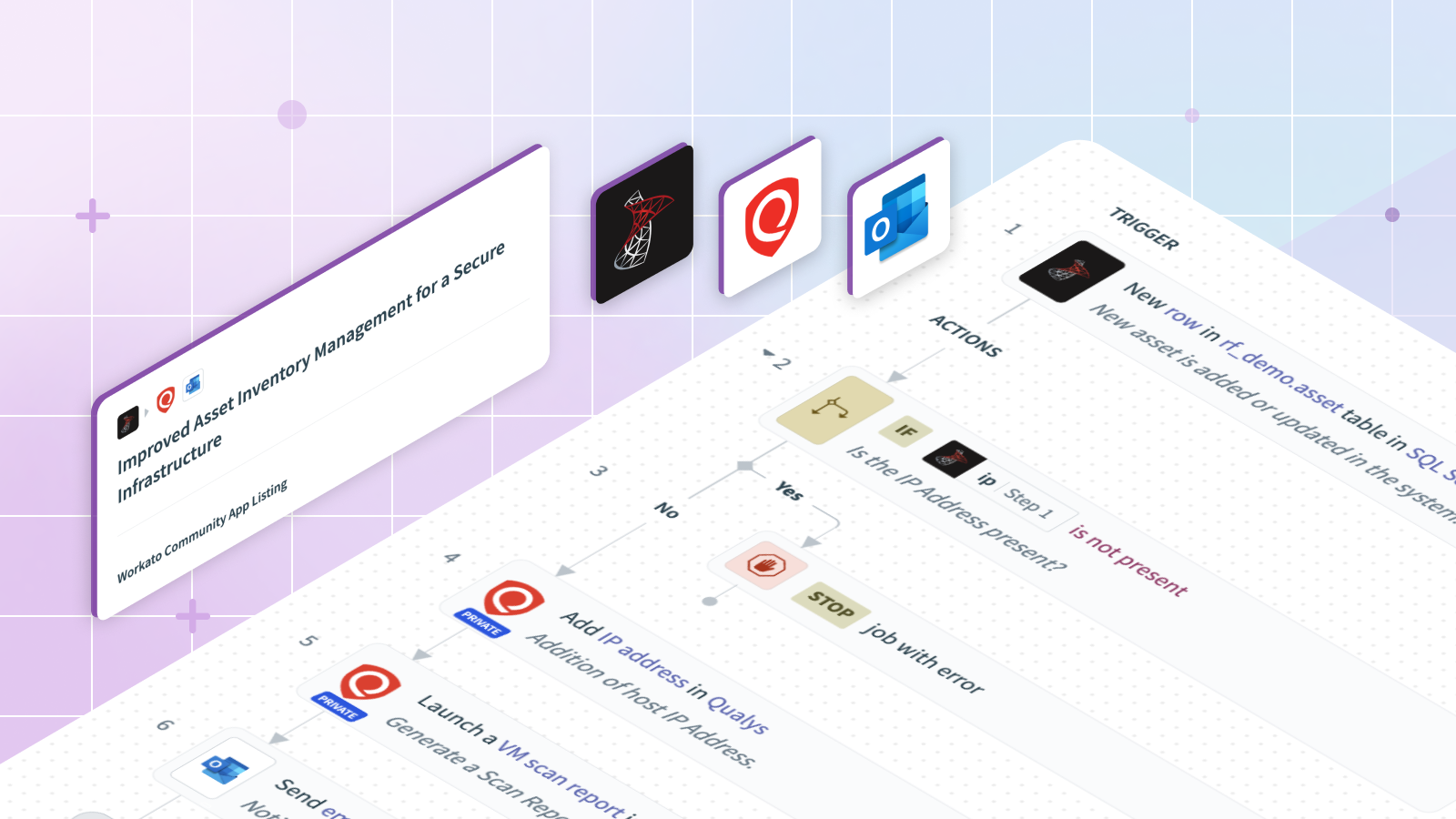
- Trigger: The automation kicks off whenever a new asset is added to the SQL Server database.
- Qualys update: It automatically updates Qualys with the host IP details of the new asset.
- Initiate scan: A VM scan is initiated in Qualys to generate a comprehensive vulnerability report.
- Email notification: The IT team is promptly notified of the scan results for further analysis and action.
Why This Automation Is Impactful:
Enhanced Visibility
By integrating asset management with automated vulnerability scans, IT teams gain real-time visibility into new assets, ensuring no asset goes unmonitored.
Improved Compliance
Regular and automated vulnerability scans help maintain compliance with industry standards and regulations, reducing the risk of penalties and breaches.
Efficient Workflow
Automation reduces the need for manual updates and checks, freeing up valuable IT resources to focus on strategic initiatives.
Proactive Security Measures
Early detection of vulnerabilities allows for swift remediation, minimizing the potential for exploitation.
Informed Decision-Making
Comprehensive reports generated from the scans provide actionable insights, empowering IT and cybersecurity teams to make well-informed decisions regarding asset management and security.
By providing enhanced visibility and compliance, this automation empowers IT and cybersecurity teams to make well-informed decisions, ultimately leading to increased productivity and an improved security infrastructure. This, in turn, safeguards your valuable data and ensures your organization remains resilient against emerging threats.
Start building in Workato
To help you get started, check out the sample recipe here for a ready-to-use version that you can easily duplicate and implement.
