Control your own data with Enterprise Key Management

We know you care deeply about the security of your data, and so do we. As the central integration and automation platform, Workato can be one of the most critical components of your data infrastructure. As our Head of Global Ops and Security Jayesh Shah points out, your automation platform accesses data and creates workflows across all of your systems, including potentially sensitive ones like HR and Finance. This means that your security needs to cover not just the core platform, but also the connections and data that your automation platform manages across systems.
If you work in a highly-regulated industry like healthcare or financial services, you may have found your choice of tools limited by the need to conform to your company’s security policies. But you shouldn’t have to choose between a product’s capabilities and security.
Data security has always been fundamental to our platform, and we’re expanding our approach with the release of Workato Enterprise Key Management (EKM). Uniquely in the iPaaS space, Workato’s EKM gives you full control over your own master encryption key. This control allows you to comply with your security policies without compromising on features and performance.
But before we look at the new capabilities offered by EKM, let’s take a look at how all of your data is already protected.
How your data is protected
Workspace-scoped master keys
Some platforms rely on a single master encryption key to encrypt all customer data. As a result, if the master key is compromised, every customer’s data is vulnerable. To eliminate this vulnerability, Workato’s encryption model uses a separate master key for each workspace.
This means that data from your workspace is kept separate from every other customer’s data. In the extremely unlikely event that one workspace is compromised, data in other workspaces are not exposed.
Multi-layer key hierarchy
Workato’s encryption key management follows a hierarchical key model. The hierarchy consists of multiple layers of keys in which higher layers of keys (parent keys) encrypt the layer below (child keys). This process is known as “wrapping”.
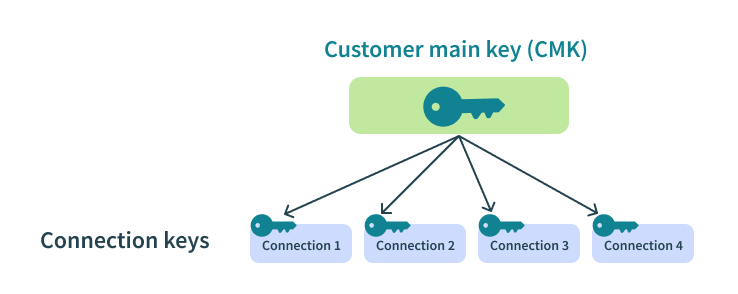
A workspace’s master key is not directly used to encrypt job or connection data. Instead, the master key encrypts other keys, which are, in turn, used to encrypt data.
For example, when encrypting connection data, each connection is encrypted by a unique connection-specific data key. The data key is, in turn, encrypted by the master key. No two connections are encrypted by the same data key.
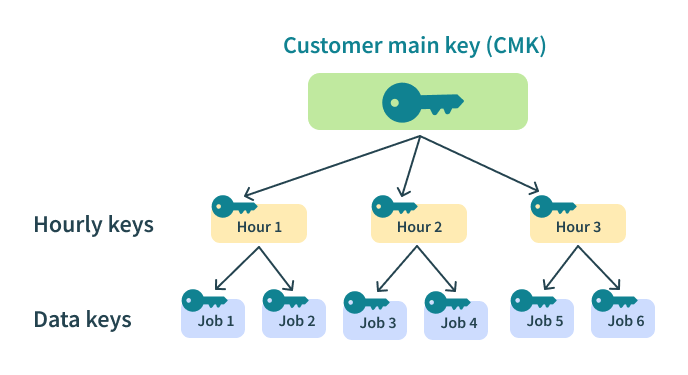
When encrypting job data, an additional level is added in the form of hourly keys. Data for each job is encrypted by a unique job key. The job key is encrypted by an intermediate key, which is rotated every hour. Each hourly key is, in turn, encrypted by the master key.
This hierarchical encryption model segregates your data. That is, no one key encrypts too much data, minimizing the potential impact of any data leak. It also means that this is achieved without the need to store large numbers of keys in plaintext.
Control your own data with Enterprise Key Management
Workspace-specific master keys and multi-level key hierarchies protect every Workato customer’s data. However, some large organizations, or companies operating in highly-regulated industries like finance and pharma, require additional control. For this reason, you may need to maintain direct control over your own encryption key.
Advantages of direct control of your encryption key
Conform to security policies
Your organization’s internal security policies may require you to conform to a specific master key rotation schedule. Controlling your own master key allows you to rotate keys whenever you need to.
Revoke access instantly
Because you control your key, you can revoke access to it at any time. Hourly and job-level keys are never stored in plaintext, so without access to your master key. Neither Workato, nor any of your Workato users, can access any of your stored data.
How it works
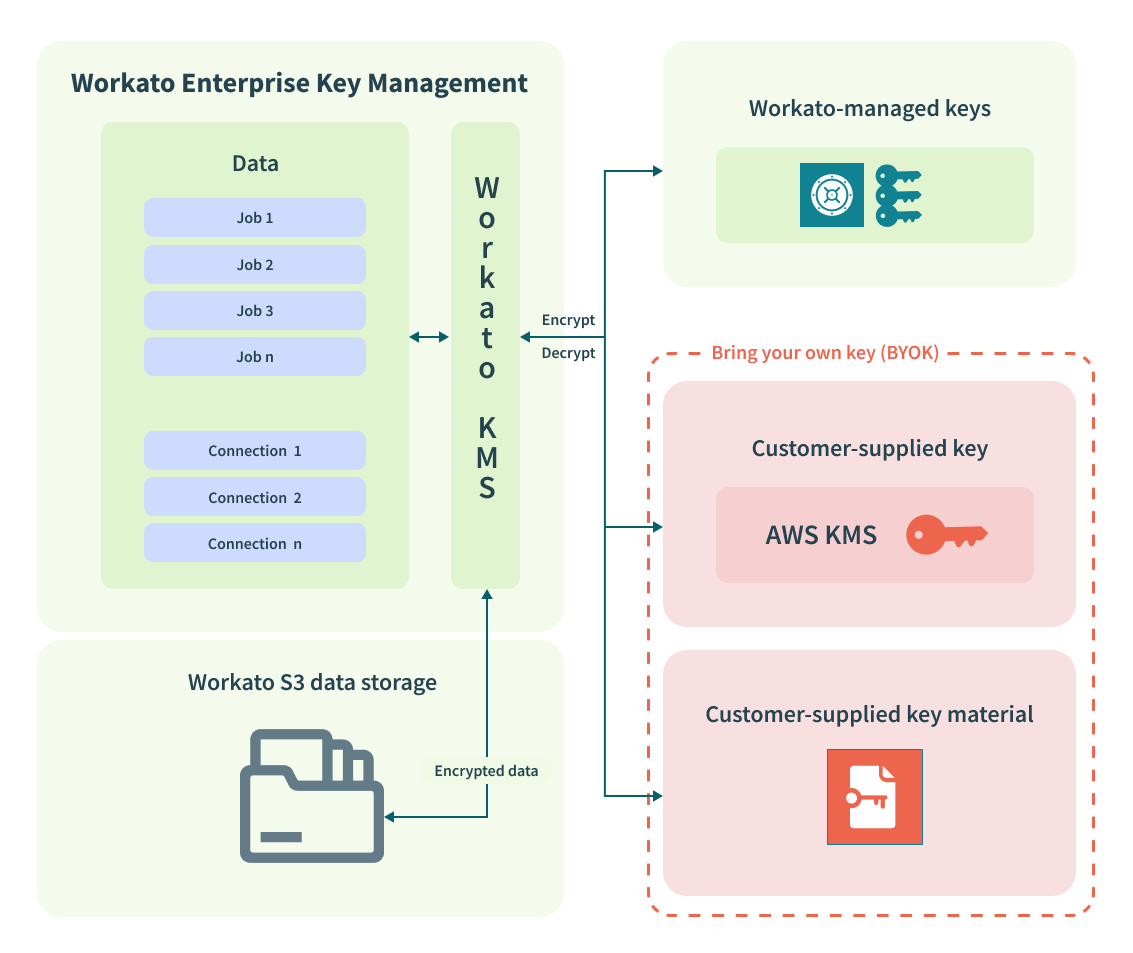
With Enterprise Key Management, you can maintain your own encryption key in a service like AWS Key Management Service (KMS) and create an access policy granting Workato access to the key. Workato uses your own encryption key to encrypt other keys in the hierarchy.
Don’t trade capability or performance for security
Managing your own encryption keys won’t impact the scope or effectiveness of your automations. EKM helps you meet your security requirements without losing out on any of the platform’s features or performance. The only difference is that you have complete control over your data.