Control secrets sprawl with AWS Secrets Manager support for your connections
What is Secrets Sprawl
Ask any security professional what’s keeping them awake at night, and secrets sprawl is near the top of the list. Secrets sprawl happens when you store your organization’s secrets, like passwords, encryption keys, and other access credentials, across many locations and apps.
Disadvantages of Secrets Sprawl
The more spread out your secrets are, the harder it is to apply any kind of reliable security policy. Something as simple as password rotation requires you first to remember where all those passwords are stored. Worse still, secret sprawl leads to increased attack surfaces. Stale, forgotten secrets off in the corners of your app ecosystem become points of vulnerability that an attacker can exploit.
As a general rule, the more you’re able to centralize the management of your secrets in a single place, the easier it is to develop and enforce a strong, coherent security policy. For this reason, many security professionals aim to centralize their secrets management in an external secrets manager, such as AWS Secrets Manager.
Automations are a fulcrum for security, processing data from across your stack, including your most sensitive functions, like payroll. So if you’re looking to centralize your secrets management, your automation platform will be one of your top priorities.
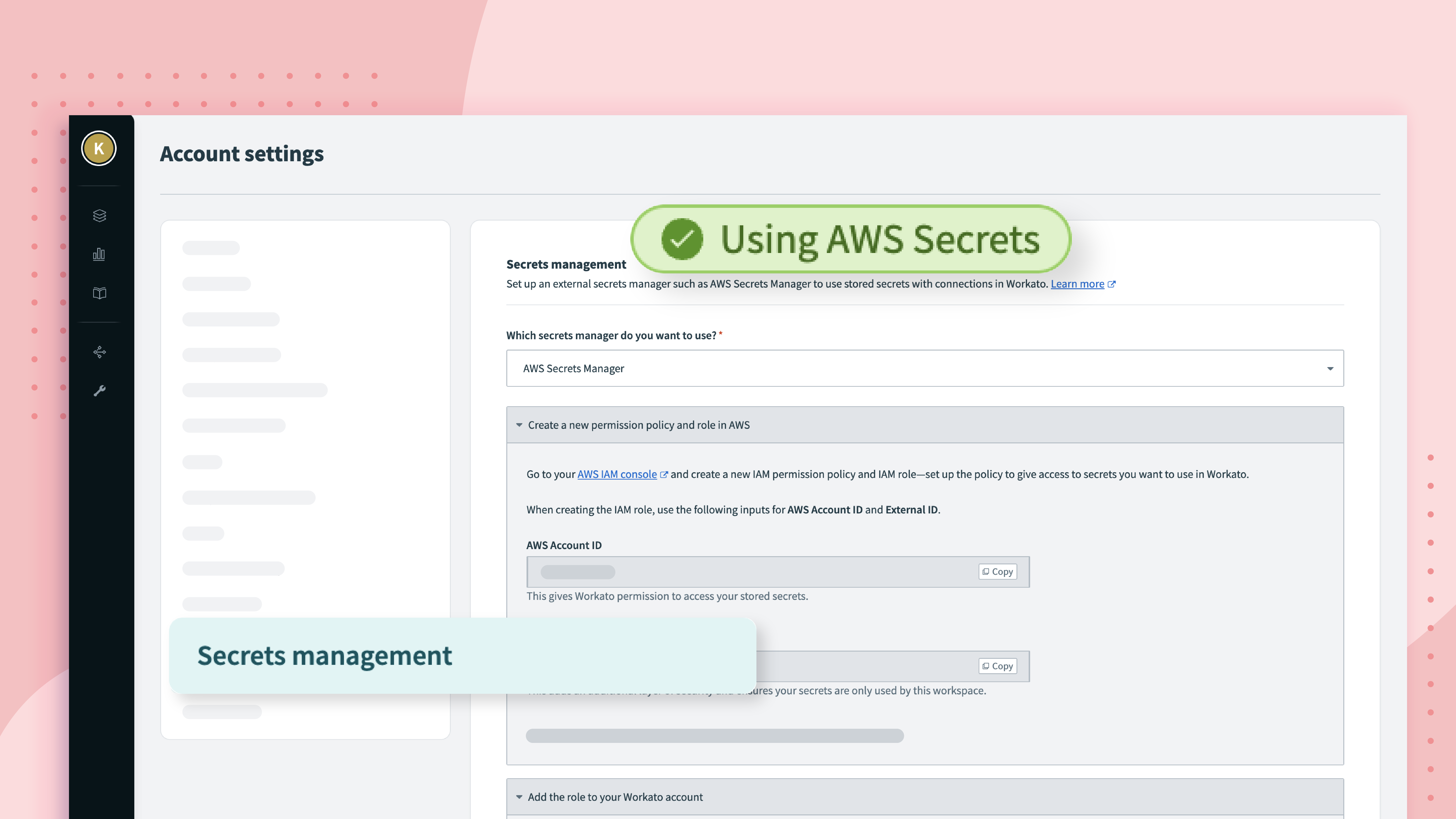
For this reason, we’re incredibly excited to announce the availability of support for Amazon’s AWS Secrets Manager. Now, you can store and manage your secrets in AWS Secrets Manager and configure Workato to retrieve the credentials when a connection is needed.
How to use AWS Secrets Manager to create connections securely with Workato
By default, when creating a connection in Workato, you supply the credentials, like username, passwords, or tokens, directly in the Workato UI. Workato stores the credentials, encrypted by a unique, connection-specific key.
When using AWS Secrets Manager, you instead store the credentials there, and create a policy that allows Workato to access them. When you create the connection in Workato, instead of supplying the credentials themselves, you supply a reference to the credentials stored in AWS.
This means that Workato can connect to your apps and databases without actually storing your credentials at all.
Benefits of Secrets Management
Many organizations require centralized secrets management to control and protect the credentials from unauthorized access and distribution. Increasingly we see demand for Workato to use credentials stored in customer-managed secrets manager. Using an external secrets manager to store your connection credentials confers several benefits:
Secrets Protection
Storing your secrets only in a dedicated secrets manager helps protect your organization against potential compromise of credentials and connections. When you integrate with AWS Secrets Manager, your credentials are not stored in Workato at all.
Centralized Secrets Management
Centralized secrets management is the opposite of secrets sprawl. With all your secrets managed in one place it’s easy to create and enforce security policies such as policy-driven storage, encryption of credentials and time-bound secret rotation. It’s also simple to audit all access to your secrets over time.
Access Control
Use of AWS Secrets Manager to establish connections in Workato gives you more control over how and when those credentials can be accessed. You can revoke Workato’s permissions to access any secrets, at any time.
How does AWS Secrets Manager work?
For detailed info on setting up AWS Secrets Manager, see the docs. As a broad overview:
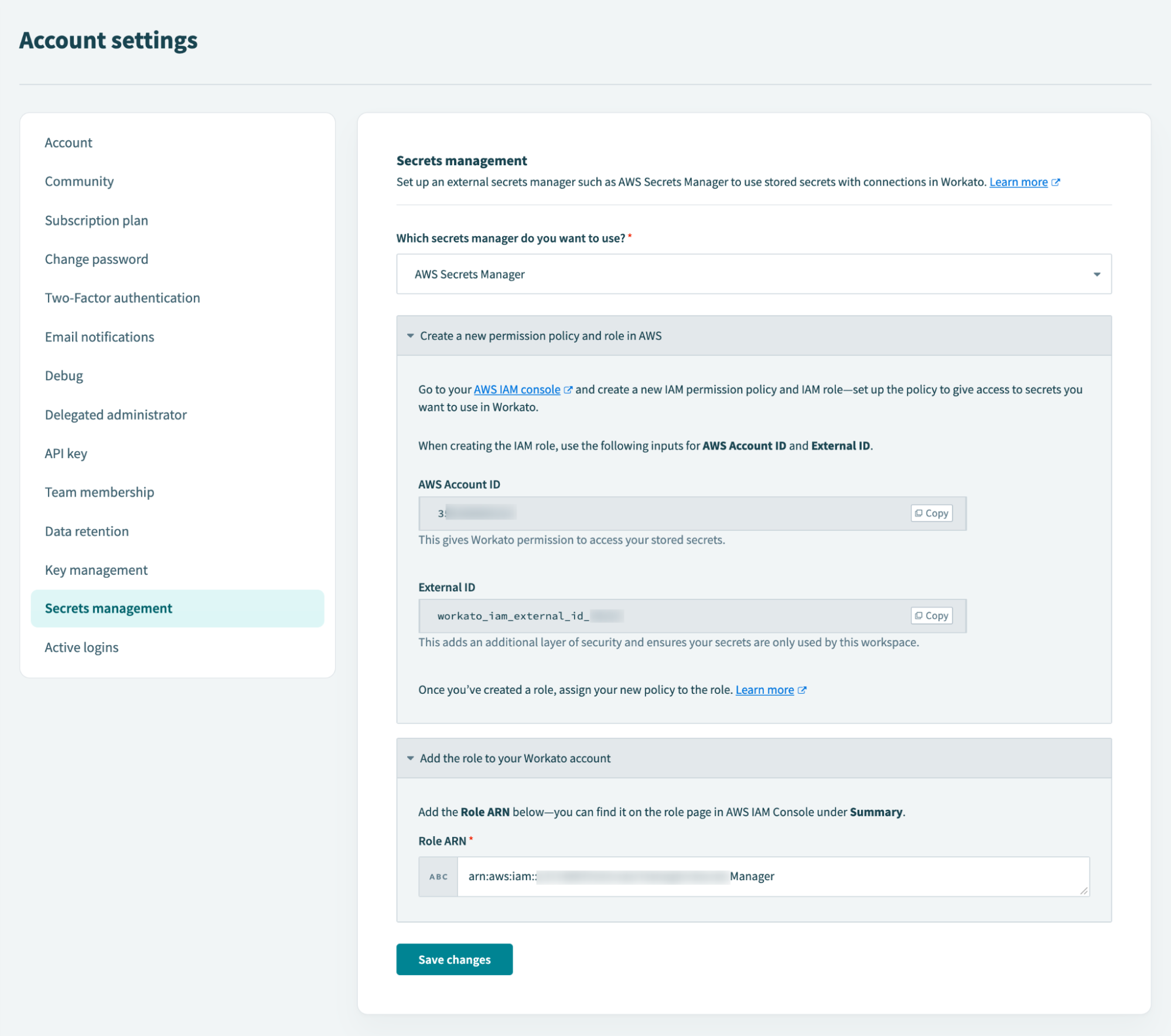
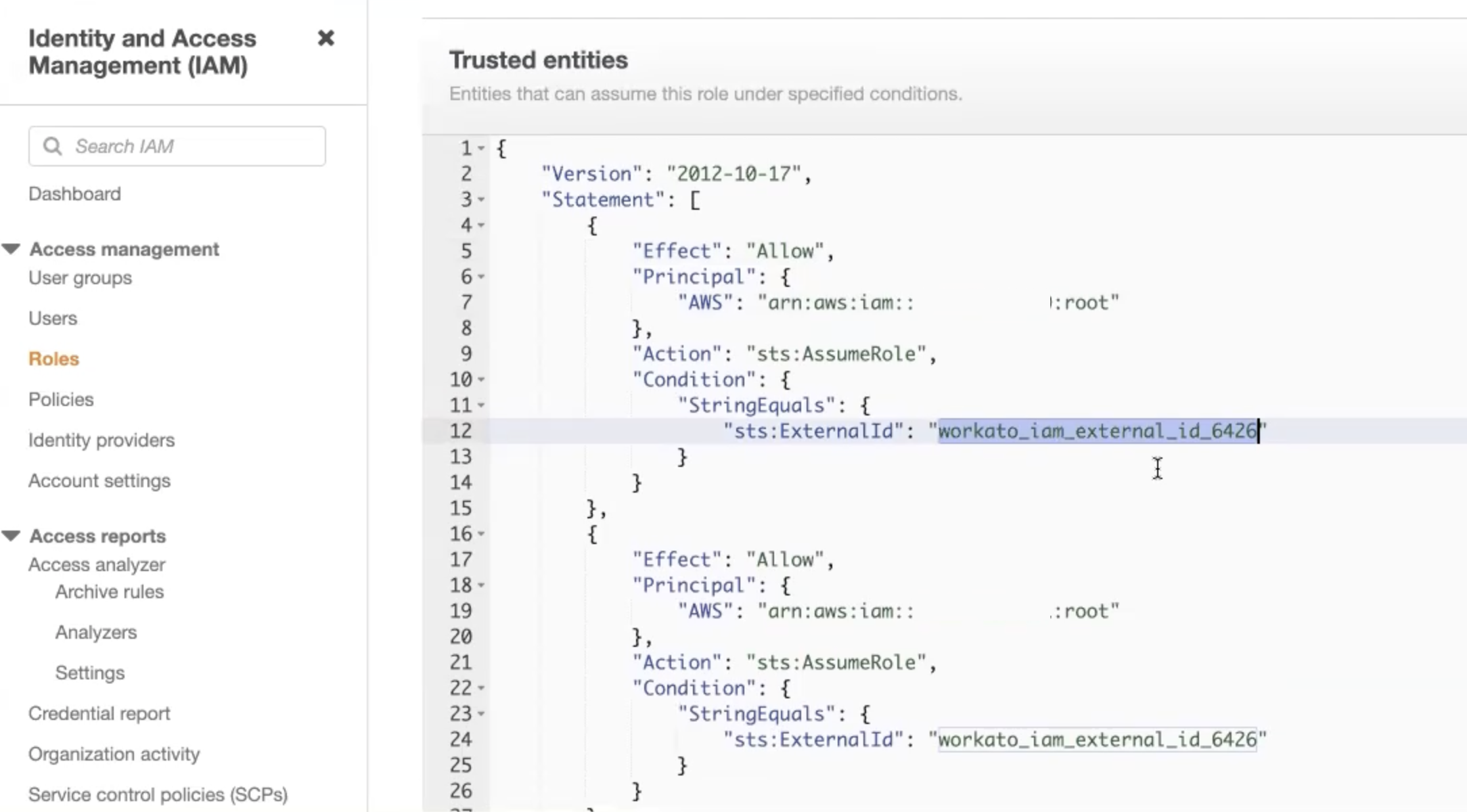
- In the Secrets management configuration you need to give permission to a designated Workato AWS account.
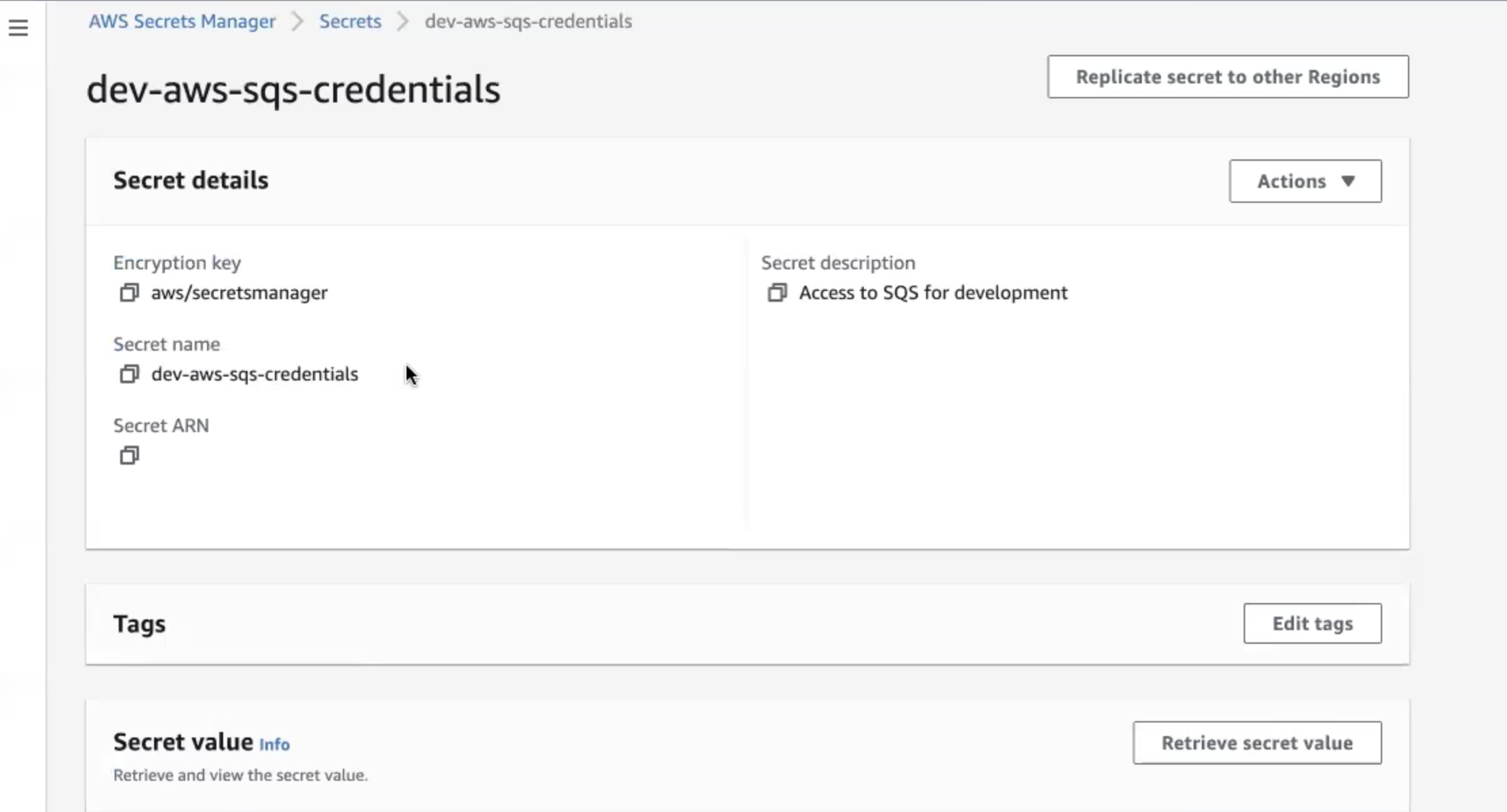
- Create your credentials directly in AWS Secrets Manger.
- Create a policy, granting Workato access to the secret.
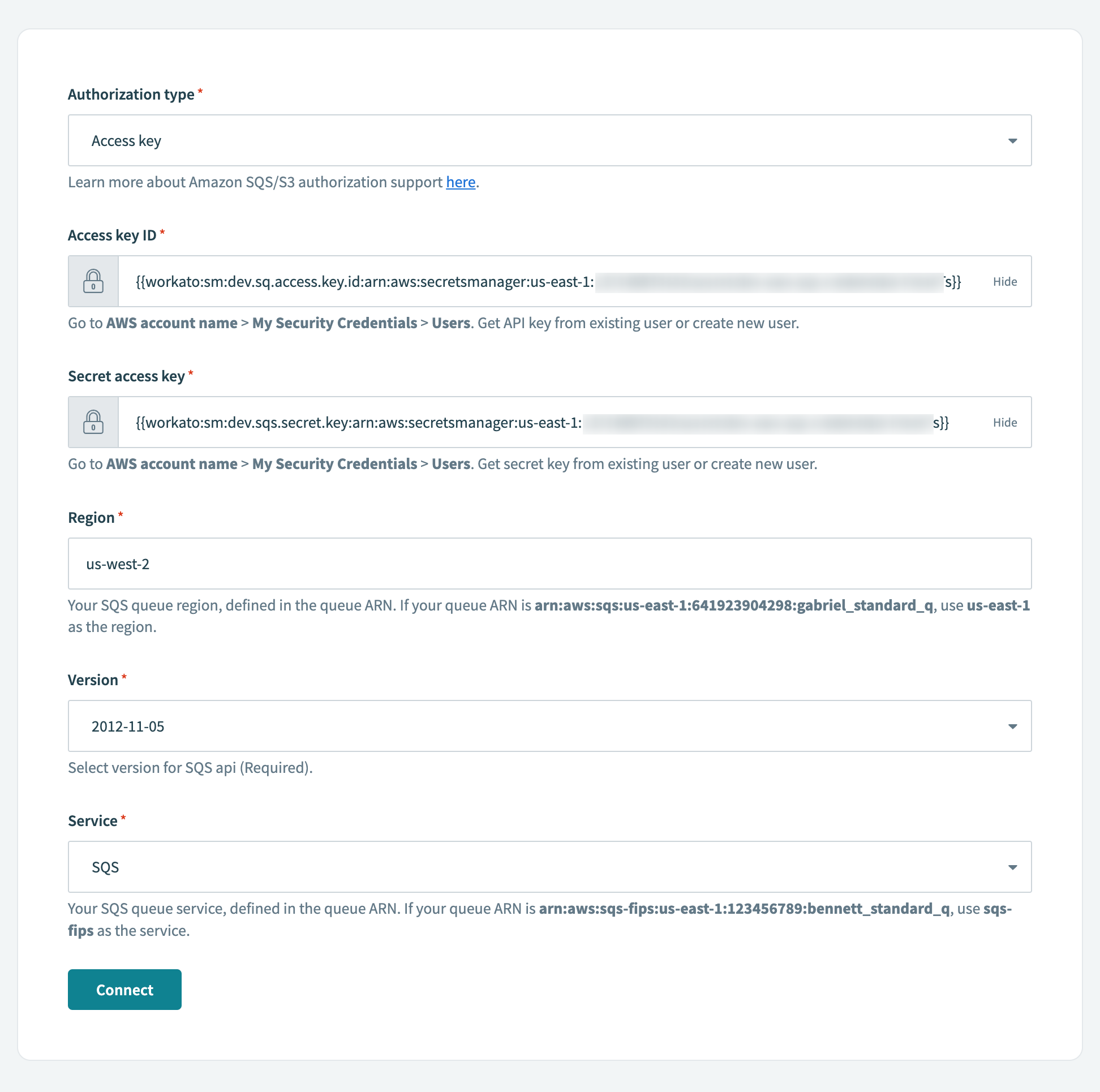
- In any connection field that requires a secret, use the pre-defined format to reference the secret name that contains the secret value. The format is:
{{workato:sm:<secret name>:<secret ARN>}}.
Frequently Asked Questions About Secrets Manager
What secrets managers can I use?
The Workato external secrets manager currently supports Amazon Web Services Secrets Manager (AWS Secrets Manager). We may add support for other popular secrets manager in the future.
Can I share secrets and other sensitive information via the secrets manager?
Yes absolutely! Workato’s external secrets manager support can retrieve the secrets value as long as Workato has permission to access it and you’re using the right format. It can be actual secrets like username, password, API tokens. It can also be any other sensitive data that is required to successfully establish a connection to your application.
What happens when the administrator removes permission or deletes the secrets?
Once you remove Workato’s permission to access the secrets, the connection will no longer be valid after the cached secret expires. Jobs may fail as no valid connection exists to execute the step in the recipe.
What happens if I update the credentials in the secrets manager?
Once you update the secrets in the secrets manager, for each connection that uses the secrets, you must disconnect and reconnect to refresh the connection with the new credentials.